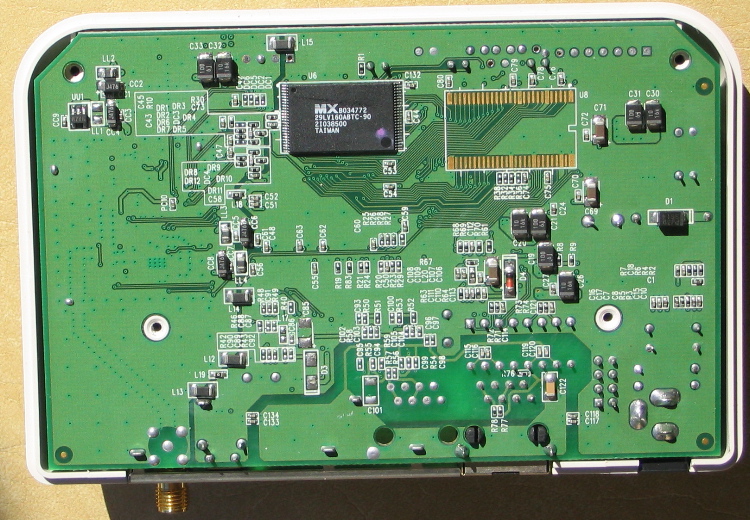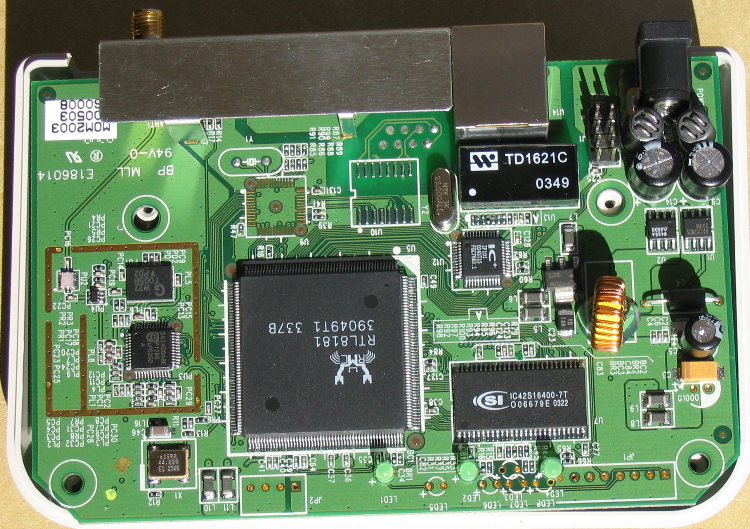
See rtl8181.sourceforge.net for more details.
Seems that the webserver for the admin interface is GoAhead, which has some known exploits. It seems that giving an url with > 64 slashes will kill the webserver, if you know MIPS shellcode, you might be able to get a root prompt.
I've compiled a Dropbear binary with the nonmips toolchain, for the demo images available at the rtl8181 site. Instructions follow:
(perhaps remove tcpdump if you won't have enough space) wget http://matt.ucc.asn.au/minitar/dropbearmulti wget http://matt.ucc.asn.au/minitar/libutil.so.0 mv libutil.so.0 /lib mv dropbearmulti /usr/sbin chmod a+rx /usr/sbin/dropbearmulti ln -s /usr/sbin/dropbearmulti /usr/sbin/dropbear ln -s /usr/sbin/dropbearmulti /usr/sbin/dropbearkey ln -s /usr/sbin/dropbearmulti /usr/bin/dbclient ln -s /usr/sbin/dropbearmulti /usr/bin/scp mkdir /dev/pts mount -t devpts devpts /dev/pts passwd root (then set a password) dropbearkey -t rsa -f /etc/dropbear_rsa_host_key (and now we actually run it): dropbear -F -E -r /etc/dropbear_rsa_host_keyI think that's all. Works for me, no idea if it'll work for you :) Dropbear was cross-compiled on OS X using the non-mips toolchain, with ./configure --disable-zlib (and appropriate cross-compiling options). Then just turned off a few options in options.h, and compiled a multibinary with everything except dropbearconvert.